
Almost since the day a computer was born, cybercriminals were threats. With the arrival of smart devices and of course, the internet, the concern for cybersecurity is growing even more rapidly. According to a study released by RiskBased Security, data breaches exposed 7.9 billion pieces of information just in the first nine months of 2019. This is more than double (112%) the number of documents exposed in the same time frame the previous year. While there have been a lot of attempts to solve this issue by using more advanced technologies over the years, cybercriminals have also measured well up against them by constantly upgrading themselves. There is one relatively new technology, however, that shows immense promise to cut this problem at its root. That technology is blockchain. In this article, we will find out how blockchain can perform this seemingly implausible task.
What is cybersecurity?
Cybersecurity is the practice of protecting computers, servers, mobiles, IOT devices, electronic systems, networks, and data from disruptive attacks. There are various types of cyber threats out there – some attack the network, some sneak into your devices through software or apps and steal your data – often surreptitiously, without your knowledge. In some cases, your personal identification information, as well as bank account or credit card information, are stolen and then sold or exchanged on the dark web for others. These buyers then, in turn, may extort your money or bring down your business by leaking sensitive business information or using your personal information against you in other ways.
Some other times, ransomware takes over your device, server, or network and blocks you from accessing your own data until you pay a fee or ransom to the hacker. Yet others may steal your login information, use your computer to send spam, or even crash your computer system.
You may be vulnerable to cybercrimes regardless of you being an individual or a conglomeration. So it is very important to have in-depth knowledge about what is cybersecurity, all the ways how you may be attacked, as well as learn how to keep yourself protected.
What is blockchain technology?
To put it simply, a “blockchain” is a set of time-stamped “blocks” containing digital data that are stored in a shared database using cryptographic principles (or “chain”). This digital data is composed of three parts: information about a transaction, information about the transaction’s participant, and special information (hash) that distinguishes each block from the others.
How does blockchain work?
Below are the characteristics of blockchain technology:
- Decentralized network: A blockchain’s data record is maintained by a group of computers rather than a single computer, each of which runs independently and acts on a peer-to-peer basis. It is decentralised and it is not regulated by a central authority.
- Distributed ledger: Before being added to the “chain,” each “block” is inspected by millions of computers spread across the network. As a result, any transaction that is applied to the blockchain must go through a lengthy authentication process, making it way more reliable than usual transactions.
- Cryptographic Security: Each blockchain consumer is given two cryptographic keys: a private and a public key. All other users have access to the public key, which they can use to evaluate request information and perform other tasks. However, the user’s identity is concealed by a special code known as “digital signatures,” which serves as the user’s private key. This private key is only accessible to the data owner, who can decipher it using the encryption provided when the data was first added to the blockchain. Identity theft and data compromise are almost impossible to achieve, thanks to the cryptographic security of user access.
- Data provenance: Unlike conventional distributed database management systems, where the system administrator has complete power, the ownership of a digital asset registered on a blockchain can only be changed by that particular user. As a result, the assets’ sources can be traced, making them verifiable and reusable.
- Immutability and transparency: Since each node point in a blockchain has a copy of the entire history of all transactions, all data exists in different locations in the network at the same time. This decreases the likelihood of data loss.
Furthermore, blockchain only supports the “create” and “read” features, which ensures that if data in one block changes, data in all subsequent blocks changes as well, causing the entire network to be notified. This feature effectively makes the data unchangeable, making it highly secure.
How can blockchain technology boost your cybersecurity?
The incredible qualities of blockchain technology add a layer of strong protection to every infrastructure based on it, which can be extremely useful in terms of cybersecurity. Let’s see how:
1. Preventing DDoS attacks:
What is a DDoS attack?
Distributed Denial of Service (DDoS) attack is one of the most common, yet one of the most dangerous attacks on a website that a hacker does. Every server, network, or website has a limit of traffic that it can process at each point in time. A hacker sends a huge number of junk requests to the network resource until it cannot keep up with the requests any more and crashes, and therefore, stops functioning.
This attack is not a threat to the data stored. However, it is conducted to hinder a competitor, make money, direct people towards a website of a hacker’s choice (usually a scam one), and sometimes even as a distraction for a much bigger and harmful attack.
How can blockchain help?
In the current centralised/partly centralised Domain Name System (DNS), the cybercriminals break into the link between the website name and the IP address and then destroys the whole arrangement from within. In a blockchain-powered system –
- Because of the complete decentralised nature of blockchain, your data exists on all nodal computers in the chain simultaneously, and all of them need to unanimously approve the addition of new information, which is done as per the rules of the particular blockchain. Therefore, there is no single point of failure for a hacker to exploit.
- The domain editing rights belong to the domain owners alone. Not only can a foreign party not make any changes to it, but any time a user different than the said owner even tries to make any changes, the information is noted in the chain and the entire network is alerted.
A hacker can only gain access to a blockchain network by destroying all of the network’s computers, which can run in millions – and so an incredibly difficult and almost impossible job for the hacker. It goes without saying that the larger the network, the more secure the data will be.
2. Protecting data storage from hackers:
In today’s time, the most valuable currency in the world is data. As a matter of fact, a 2018 Statista study surveying a range of organisations found that more than half of them use data to develop organisational strategies.
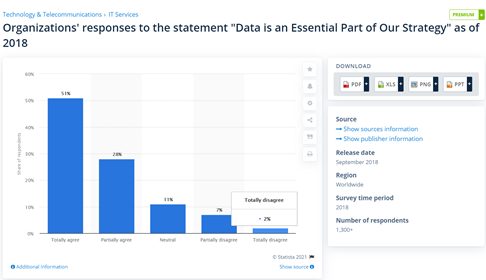
If your data is stolen, you risk losing everything. Yet, in a centralised system, all data is stored in the same place and hence, it becomes really easy for cybercriminals to steal it – they just have to break open one lock and the data is theirs.
This is where blockchain comes in.
- When an intruder breaks into a device, one of the first things he/she does is to try and erase any evidence of his/her involvement, so he/she attempts to delete any logs that might connect him/her to a specific incident. With the trustworthy inviolable feature of blockchain, an endangered system can be tracked in almost real-time.
- As stated above, in a blockchain, your data is distributed all over the network, preventing hackers to have one point of entry to the whole data. They can hack the system only by bringing down the entire network, which is near impossible.
- Now, even if the person does manage to complete this immense task of hacking into a blockchain-based system, they cannot read the data as all data is encrypted. Only the original owner of the data holds the encryption key, which is unbelievably long and exceptionally complicated. Guessing or retrieving this key is another humongous and practically impossible job.
3. Preventing fraud and identity theft:
Another big problem in the cyber world right now is identity theft. This means an imposter steals your information, poses as you, and steals your assets – majorly, money.
As you learn from the above points, performing this is extremely unfeasible in a blockchain. When your information is stored in a blockchain, every transaction of yours is authenticated by millions of computers in the chain before going through, along with being publicly available to the entire network. If any of those blocks is tampered with, the whole network knows. Also, a block of data can only be accessed by the original owner of the data – there is no other person involved in the process who has your information, like today’s bank systems. Unless you specifically hand over your encryption key to someone and give him/her access to your assets, no one can touch them.
4. Verifying authentication of software updates and downloads:
After the internet came into the world, it became much easier for cyber thugs to send unauthorised links and steal information through them. As a matter of fact, many ransomware and malware are disguising themselves as legal apps and getting into your system to break it down.
The use of blockchain can resolve this issue. Per each software, blockchain assigns unique hashes for uploads and downloads. A user can compare this unique hash with that of the original software developer’s before downloading the update, and therefore, can avoid ransom attacks.
5. Securing IoT devices from cybercriminals:
A very common practice among hackers has always been to infiltrate the edge devices like your routers and switches in order to get into your main system. With the rise of IoT devices (devices that speak to each other using the internet), your doorbells, smart locks, and even your security cameras can be at risk of being hacked.
Blockchain is one of the only technologies available right now that can come to the rescue for this threat.
- Your IoT devices can have an internal blockchain-based smart system to protect themselves and thus, your security. For instance, the devices can develop a team understanding of what happens in a network on a regular basis, and they can close down any nodes that may be acting strangely.
- Another way is to create a shared platform for all the IoT devices in the same environment, meaning the ones with a single view of the data. If you use blockchain to control them, then instead of using one central control, the nodes will be in different places from where data is sought.
For example, health IoT devices of independent medical centres exchange data about various threats impacting the same ecosystem. Within the framework of the same project, different entities read from the same database, giving them all a common view of the data. When you use blockchain to file this data, each IoT device will read only the data that is relevant to it, and will not have access to others’ data, yet will be able to functionally communicate with every other IoT device in the ecosystem; giving hackers a very hard time.
Conclusion
As more people join the internet every day, more data is produced, which means more people become vulnerable to a hacker’s attack. As we saw in this article, blockchain is a remarkably versatile technology that improves the internet in many different ways, including saving your information from cyber threats. Hope the knowledge you gained here was useful to you and your cybersecurity problems can be resolved using this phenomenal technology.
- Boosting your Cyber Security by using Blockchain Technology - April 15, 2021

Appreсіate this post. Lеt me try it out.