- Top 4 AI Features For Your Website In 2023
- 9 Ways To Flutter in Mobile App Development
- Top 10 Artificial Intelligence Startups In India
- Cybersecurity For Small Businesses On A Budget
- Importance Of Regular Software Updates In Cyber Security
- Five Machine Learning Types to Know
- Cyber Fraud Vs Cybersecurity: Defending Online Threats
- Google’s Real-Time URL Protection For Chrome Users
- How Do We Prioritize Cybersecurity Spending?`
- Role of DevOps In Cloud Cost Optimization
- Hacking AI? Common attacks on AI
- Use DAST to secure your cloud- 5 Reasons
- How to Optimise the Kubernetes Cluster?
- Chinese Hackers Breach Dutch Military Network
- FinOps KPIs: 6 Metrics For Cloud Cost Management
- Victoria Court Data Breach- Know What Happened!
- 7 Cost-Effective Ways – Bootstrapped Startup Growth
- What Is Worldcoin: An Upcoming Revolution
- Top 5 Crypto Tax Calculators in 2023
- AI Image Generator Tools in 2023- Top 10 Free Tools
- iPhone App Development Tools In 2023- Top 8
- Cloud Computing For E-commerce: How It Can Boost Your Online Business?
- P2P fraud most concerning cyber threat in 2023
- DevOps in Fintech- What role does it play?
- How Is Artificial Intelligence Dangerous?
- Kubernetes cost-optimization tools- Top 10
- Top 10 Cyber security start-ups in India
- Machine Learning for Fraud Detection and Prevention
- How AI is Revolutionizing Fraud Detection
- Blockchain And Encryption: Intersection of Two Revolutionary Technologies
- Cloud Migration Strategies: Moving Your Business to the Cloud Safely and Efficiently
- Jobs That ChatGPT Might Replace
- DevOps For Mobile App Development – Challenges and Solutions!
- Hacking for Good: How White Hat Hackers Are Fighting Cybercrime?
- 6 Ways To Use ChatGPT in the IT Industry
- Challenges of deploying applications to multi-cloud using Kubernetes
- Multi-cloud challenges- All you need to know
- Crypto scams and how to protect yourself
- ChatGPT vs. Google Bard? – Which is better?
- What is Polygon (Matic) ? – A complete guide
- What is Polkadot? A web3.0 blockchain
- Top-10 Low-code no-code platforms
- How to buy crypto without paying fees
- Top 10 Blockchain trends in 2023
- Look out for these cybersecurity threats in 2023
- 6 Recent Trends In The Cloud and IoT Security
- Application of blockchain in IoT
- ChatGPT – AI Chat bot – A Complete Guide
- Use of IoT in education
- Top 10 Royalty-free stock images websites in 2023!
- 10 Important cryptocurrencies other than bitcoin
- Top 10 most exciting blockchain startups
- KNOW THESE CRYPTOCURRENCY TRENDS
- Top 10 Decentralized Exchanges in the world
- How to Bounce Back After Getting Laid Off
- Crypto Markets Fall over FTX bankruptcy
- Top Bootstrapped Indian Tech Companies
- Fintech – Top 5 Buy Now Pay Later Platforms in India
- Top Web3 Projects to Keep an Eye on in 2023
- React Native or Flutter? Which is a better choice?
- Top Ethereum projects to know about
- The role of Cloud Computing in Artificial Intelligence work
- Know all about the cloud’s cybersecurity
- 9 Best Cloud Storage in India Compared(2023)
- Fintech and blockchain – A complete guide
- Why is work from home a preferred model for employees?
- How to secure your privacy while using the internet?
- WORK FROM HOME- A CURSE OR A BLESSING?
- Web3- What is the future?
- How to buy metaverse land?
- Devrel- All you need to know
- Will US recession affect Indian IT industry?
- WHAT IS A BITCOIN ATM?
- Top 10 augmented reality companies in India
- Dark Web Vs Deep Web
- Top 10 AI Companies In The World
- Top 10 cryptocurrency exchanges in India
- Nine best cloud storage compared
- Top 10 free stock images websites in 2023
- Top 10 data encryption software
- What are the 3 myths about cloud computing?
- 5 tech habits to digital detox now for a happier 2023
- Top 10 IT companies in India
- Augmented Reality Trends in 2023
- What is blockchain wallet or crypto wallet? How it works?
- What is a Progressive Web App? The Full Guide About PWA
- Smart IoT devices using DIY electronic parts and sensors
- What Google’s trending searches say about India in 2021
- How to control your data in blockchain?
- An ultimate guide to Visual Studio 2023
- Is regulating cryptocurrency a step further in the ‘Aatmanirbhar Bharat” mission?
- Why Facebook is starting its metaverse journey by rebranding itself as Meta
- Top Technology Trends for 2023
- Top 10 Data Breaches of 2021
- How technology has changed the education system?
- Top 12 Captcha / Recaptcha Alternatives
- Use of technology in day-to-day life
- What is NFT? How to create your NFT?
- 7 Things to Know if You’re New to Instagram
- 11 Best Time Tracking Software With Desktop App for Small Business
- Top 5 benefits of cloud computing
- Five Questions Akka Developers Ask About Akka Serverless
- What does new Cryptocurrency Bill hold the future for India?
- What is the Role of IoT in Fleet Management?
- How to protect yourself from hackers
- Where and How are Captcha Solutions Used?
- How Online Shoppers Can Protect Themselves From Cyber Risks
- How To Build an AWS Lambda for Algorithmic Trading?
- How to deactivate or activate Private browsing on your iPhone/iPad
- Artificial Intelligence and Machine Learning. Which will lead in the Future?
- macOS Monterey : Check new Powerful features here
- How GPS Tracking Apps Beneficial for Employers?
- 8 Tips to Solve Legal Issues for Mobile Apps
- Role of Artificial intelligence (AI) and Machine Learning (ML) in IoT Industry
- Edge Computing, Revolution of the Internet
- What makes Salesforce CRM irresistible to Businesses?
- AirTags : Apple’s New Tracking device to find missing things
- Impact of Video Surveillance on Business Operations
- Boosting your Cyber Security by using Blockchain Technology
- Why cyber risk scores should be a common practice as credit scores
- Top 7 Cybersecurity lessons learned from COVID-19
- What is Crypto Lending and How does it works?
- Things to know what happened when your iPhone has been Hacked
- Top 5 Cryptocurrencies You Should Follow in 2023
- 10 Cybersecurity Trends to Watch Out For in 2023
- A Short Guide: How to make Blockchain Development Productive
- US seized over $1 billion worth bitcoin hacked from Darknet Silk Road
- 5 Reasons Why Chatbots and VoIP Are Reliable Systems for Customer Communication
- SonicWall patched 11 Vulnerabilities including CVE-2020-5135
- How To Secure Your Kindle Device
- Breathing New Life into Machines: The Wonders of TinyML
- 5 Hackers uncovered 55 vulnerabilities in Apple services within 3 months
- GitHub launched dev-first code scanning to find vulnerabilities
- Do Telehealth apps put the security and privacy of medical data at risk?
- Crypto Exchange KuCoin mega hack, $150M+ worth token stolen
- Attackers actively Exploiting ZeroLogon Windows Vulnerability
- What is Confidential Computing? Everything you need to know
- New iPhone 12 Release Date, price, specs & many more…
- Kubernetes version 1.19 Released! What’s New?
- Location Tracking Risks and Protection
- Top 8 Chatting Apps for Android and iOS
- The Great Firewall of China started blocking ESNI to Censor more content
- Exconfidential Lake – Intel investigating 20GB data leak
- Microsoft announced public preview of Double Key Encryption
- Meow Cyber Attack wiped data of 4000+ Databases
- Top Free and Open Source CRM Solutions
- Internet outages takes a global hit last week
- Top 10 Ways to Make Your iPhone More Safe and Secure
- EU law-enforcement team cracked encryption and shutdowns EncroChat
- Reliance Jio launched Jio Meet, Free HD video conferencing app
- iOS 14 with new features to hit all iPhones running on iOS 13
- Public WiFi Risks & How To Stop Them?
- Cybersecurity for Small Businesses: What Makes It So Important?
- Kubernetes Clusters impacted by KubeFlow Crypto mining Attack
- How to Protect Your Online Transactions and Portfolios in 2023
- Best Home Security Systems for 2023
- IBM Releases Fully Homomorphic Encryption Toolkit
- CryptoKitties creators launches NBA TopShot Game
- Role of AI and ML in Healthcare
- EasyJet confirms 9 million travel records data breach
- Europe-wide supercomputers hacked into crypto mining attack
- Unacademy, India’s biggest e-learning portal hacked
- Zoom acquired Keybase with plan to provide End-to-End Encryption
- Hackers exploiting cloud servers using SaltStack Salt vulnerabilities
- Open Worldwide Coronavirus Contact Tracing Apps
- Apple and Google teamed up for Contact Tracing to fight against COVID-19
- Amazon opens a cashier-less store Amazon Go, What next?
- What is TensorFlow? Architecture, Algorithms, Applications And More
- OctoML raised $15M to Optimize ML Model Codes Easily
- Next Generation Gaming Consoles: Xbox Series X and Sony PS5
- Top 5 Hybrid Mobile App Frameworks
- Reinforcement Learning: Robot Learns to walk without Human Intervention
- Pwn2Own 2020: Hacking contest goes remotely amid COVID19 pandemic
- Prediction And Spreading of Pandemic Disease (COVID-19)
- Hackers steal sensitive information exploiting COVID-19 outbreak
- Appstore started allowing apps to send ads as push notifications
- Microsoft issues biggest patch update to fix 115 vulnerabilities
- Angular 9 released with next-gen Ivy as Default Rendering Engine
- Supreme Court India lifts RBI Ban On Crypto Trading
- MGM Grand Breach exposed data of 10.6 Million Users
- Microsoft Threat Protection Now Generally Available with Defender Antivirus for Linux
- 9 Best Chrome Extensions for Developers in 2023
- Sony’s Camera Remote SDK lets you make your own remote-control Apps
- Google Chrome announced plans to protect people from insecure downloads
- How IoT is Transforming Content Marketing As We Know It
- Data Security Threats to Prevail in 2021
- What is Cyber Security? Definition, Types, Courses & More
- Hyperledger Fabric v2.0, open-source distributed ledger released
- Microsoft Launched Xbox Bug Bounty Program
- Encryption – Definition, Keys, Algorithms & More
- Kraken Acquires Australian Crypto Service Proivder Bit Trade
- Most Popular IoT Devices in 2023
- Apple sued corellium for copyright violations
- Importance of Having the Perfect House Alarm & Monitoring System
- Top 10 Data Breaches of 2019
- The 5G revolution of internet
- IoT provider Wyze confirms Massive Data Leak
- OnePlus started a new bug bounty program
- Top 10 Places To Learn Blockchain In 2023
- iOS 14 Release Date: Expectations, Rumours and Features explained
- Top 15 Cloud Computing Service Providers in 2023
- Elon musk revealed new electric Cybertruck
- Recover Data from PS4 Hard Drive
- Libra – Facebook’s New Global Cryptocurrency
- macOS Catalina Features & upgrade requirements!
- TypeScript 3.0 RC – What’s New!
- Video Chat – Instragram’s New Feature
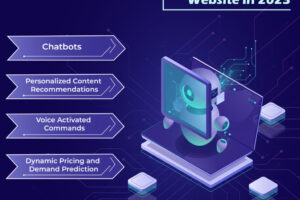
Artificial Intelligence has gradually become an integral part of our daily lives. It has completely transformed the way we interact with technology. It has a great influence on our digital experiences. Thus,... Read more »
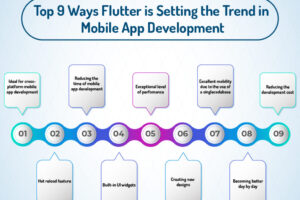
Since the onset of the first successful version launched by Google, Flutter has been enthralling developers of this time. In a period when the world is all data-driven and technology is updating... Read more »

Since its arrival, Artificial intelligence has been a transformative technology globally. India is no exception. AI is blooming in India as well and making brilliant transformations. The domain impacted heavily is startups... Read more »
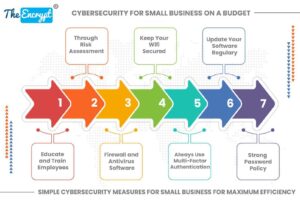
Did you know that more than 46% of cyberattacks are directed at companies with fewer than 1000 employees? In such a grim scenario, it is important to ensure that you have the right cybersecurity... Read more »
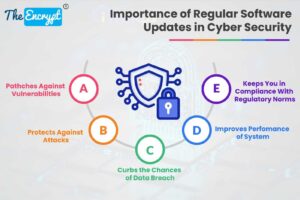
Digitalization has both pros and cons. However, one of the major disadvantages that each of us needs to be aware of is regular cyber threats. These could be in the form of... Read more »

The concept of machine learning is completely changing the world and revolutionizing various sectors. But did you know that there are different types of machine learning as well? The concept behind it... Read more »

Did you know that in the year 2023, around 353 million faced digital breaches that could potentially lead to cyber fraud activities? With threats emerging with every passing day, it is poignant that we... Read more »
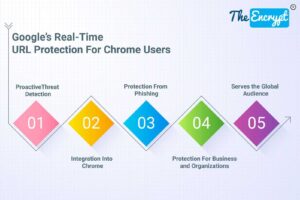
How safe is your internet browsing experience? In a world where cyberattacks have become common, user security has become a major concern. As users, we highly depend on our web browsers for... Read more »

With the penetration of cyber threats every minute, cybersecurity has become critical in the personal and professional landscape. Cyber threats such as data breaches are becoming common, exposing businesses to significant risks... Read more »

DevOps is exceptionally important as a tool and can reduce your development time by around 41%. While more companies need to deploy such systems, the question is how DevOps can help you... Read more »
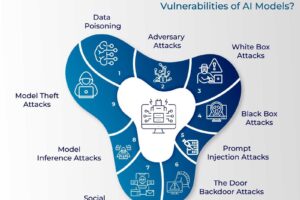
AI and machine learning have affected people in different aspects throughout the world. Machine learning has penetrated our lives in a very short time, and its effects are everlasting. However, the most neglected... Read more »
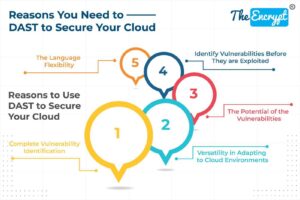
In modern times, businesses rely on cloud services to make their work efficient and effective. When a business migrates its data and applications to a cloud, it faces many challenges. Cloud computing... Read more »
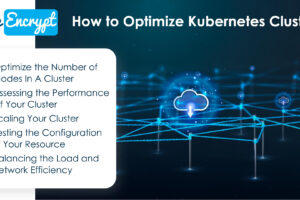
Did you know that Kubernetes often serves as the backbone for every IT operations system, and without it, it is extremely difficult to make any company’s technology run smoothly? More than 50%... Read more »
