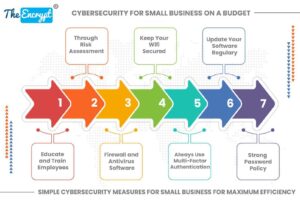
Did you know that more than 46% of cyberattacks are directed at companies with fewer than 1000 employees? In such a grim scenario, it is important to ensure that you have the right cybersecurity... Read more »
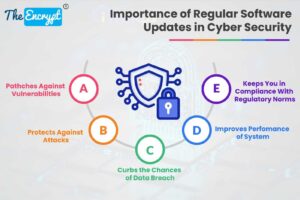
Digitalization has both pros and cons. However, one of the major disadvantages that each of us needs to be aware of is regular cyber threats. These could be in the form of... Read more »

With the penetration of cyber threats every minute, cybersecurity has become critical in the personal and professional landscape. Cyber threats such as data breaches are becoming common, exposing businesses to significant risks... Read more »
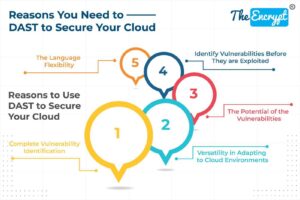
In modern times, businesses rely on cloud services to make their work efficient and effective. When a business migrates its data and applications to a cloud, it faces many challenges. Cloud computing... Read more »

The Dutch Military Intelligence recently broke the news that a group of Chinese state-backed military officers broke into a Dutch Military Network. Reports have pointed out that this breach was down in... Read more »

Peer-to-peer fraud, or P2P fraud, is when thieves utilize peer-to-peer payment systems to steal money from legitimate users. They accomplish this through various methods, including overpayment frauds and the theft of login... Read more »

Technology is evolving at a fast pace. Every sector and organization relies heavily on the internet for data storage and transfer. However, such data is prone to cyberattacks, with hackers ready to... Read more »

Whenever we mention the term “hacking”, the first thing that crosses our mind is that it is illegal. But just like every coin has a flip side, the definition of hacking also... Read more »

Have you heard of crypto scams before? Scammers want your cryptocurrency just like they want your money in the bank account. To keep your cryptocurrency safe, you should know the warning signs... Read more »

Cybersecurity threats are always on the rise. Cybercriminals are moving way ahead of cybersecurity professionals, honing their skills to break through any cybersecurity walls. The recent data from many surveys show the... Read more »
